Navigating the Evolving Landscape: Cybersecurity Industry Trends in 2023
Related Articles: Navigating the Evolving Landscape: Cybersecurity Industry Trends in 2023
Introduction
With great pleasure, we will explore the intriguing topic related to Navigating the Evolving Landscape: Cybersecurity Industry Trends in 2023. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Navigating the Evolving Landscape: Cybersecurity Industry Trends in 2023
- 2 Introduction
- 3 Navigating the Evolving Landscape: Cybersecurity Industry Trends in 2023
- 3.1 1. The Rise of Zero Trust Security
- 3.2 2. The Growing Importance of AI and Machine Learning in Cybersecurity
- 3.3 3. The Rise of Cloud-Native Security
- 3.4 4. The Growing Threat of Ransomware
- 3.5 5. The Importance of Cybersecurity Awareness Training
- 3.6 6. The Growing Need for Cybersecurity Talent
- 3.7 7. The Increasing Importance of Compliance and Regulations
- 3.8 8. The Growing Use of Blockchain Technology in Cybersecurity
- 3.9 Related Searches:
- 3.10 FAQs by Cybersecurity Industry Trends:
- 3.11 Tips by Cybersecurity Industry Trends:
- 3.12 Conclusion by Cybersecurity Industry Trends:
- 4 Closure
Navigating the Evolving Landscape: Cybersecurity Industry Trends in 2023
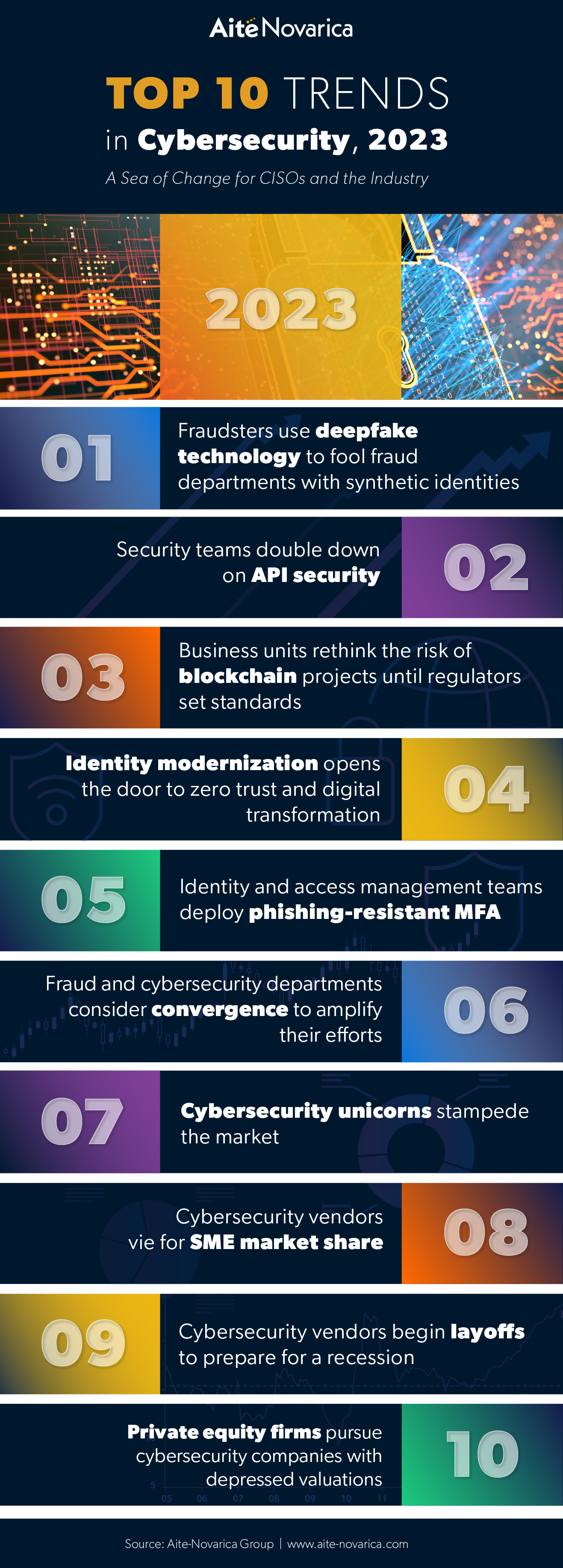
The cybersecurity landscape is in a constant state of flux, driven by the relentless evolution of technology and the ever-increasing sophistication of cyber threats. Understanding the key cybersecurity industry trends is crucial for organizations of all sizes, as it allows them to proactively adapt their security strategies and stay ahead of the curve.
This comprehensive exploration delves into the most prominent cybersecurity industry trends shaping the industry in 2023, providing insights into their significance and potential impact on the future of cybersecurity.
1. The Rise of Zero Trust Security
Zero trust security is a foundational shift in security philosophy, moving away from the traditional perimeter-based approach to a model that assumes no user or device can be trusted by default. This trend emphasizes continuous verification and authentication, granular access controls, and robust data protection mechanisms.
Benefits of Zero Trust:
- Enhanced Security Posture: Zero trust eliminates the inherent vulnerabilities associated with trusting all users and devices within a network, effectively reducing the attack surface.
- Improved Data Protection: By implementing strict access controls and continuous verification, zero trust safeguards sensitive data from unauthorized access, even in the event of a breach.
- Increased Resilience: The granular access controls and continuous monitoring inherent in zero trust enhance the overall resilience of an organization’s systems and data, making them more resistant to attacks.
Implementation Considerations:
- Comprehensive Policy Enforcement: Organizations must define and enforce comprehensive zero trust policies across all systems and devices, ensuring consistent security measures.
- Advanced Technologies: Implementing zero trust requires leveraging advanced technologies like multi-factor authentication, micro-segmentation, and data loss prevention (DLP) solutions.
- Cultural Shift: Implementing zero trust requires a cultural shift within the organization, fostering a security-conscious mindset and encouraging user adoption of security best practices.
2. The Growing Importance of AI and Machine Learning in Cybersecurity
Artificial intelligence (AI) and machine learning (ML) are rapidly transforming the cybersecurity landscape, enabling organizations to automate threat detection, improve incident response, and enhance overall security posture.
Applications of AI and ML in Cybersecurity:
- Threat Detection and Prevention: AI and ML algorithms can analyze vast amounts of data to identify suspicious patterns and predict potential threats, enabling proactive security measures.
- Security Information and Event Management (SIEM): AI-powered SIEM systems can automate log analysis, anomaly detection, and incident response, providing faster and more efficient threat identification and mitigation.
- Vulnerability Management: AI and ML can automate vulnerability scanning, prioritize remediation efforts, and provide insights into potential attack vectors.
- Phishing Detection: AI algorithms can detect and block phishing emails and websites, reducing the risk of social engineering attacks.
Challenges and Considerations:
- Data Quality and Biases: The effectiveness of AI and ML models heavily depends on the quality and diversity of training data. Biases in training data can lead to inaccurate results and perpetuate existing inequalities.
- Explainability and Transparency: AI and ML models often operate as black boxes, making it difficult to understand their decision-making processes and troubleshoot errors.
- Ethical Considerations: The use of AI in cybersecurity raises ethical concerns about privacy, bias, and potential misuse.
3. The Rise of Cloud-Native Security
As organizations increasingly adopt cloud computing, cloud-native security has become essential to protect data and applications in the cloud environment. Cloud-native security focuses on integrating security controls throughout the development lifecycle, ensuring that security is built into the cloud infrastructure from the ground up.
Key Elements of Cloud-Native Security:
- Infrastructure as Code (IaC): IaC allows organizations to define and manage cloud resources using code, enabling automation, repeatability, and increased security.
- Serverless Security: Serverless computing introduces unique security challenges, requiring specific security measures to protect data and applications running in serverless environments.
- Container Security: Containerization technologies like Docker and Kubernetes require robust security measures to protect containers from attacks and ensure secure communication.
- Cloud Security Posture Management (CSPM): CSPM tools continuously monitor cloud environments for misconfigurations, vulnerabilities, and compliance violations, providing proactive security insights.
Challenges and Considerations:
- Shared Responsibility Model: In cloud environments, security responsibilities are shared between the cloud provider and the organization. Understanding and adhering to the shared responsibility model is crucial for effective cloud security.
- Cloud Security Skills Gap: The rapid adoption of cloud computing has created a skills gap in cloud security. Organizations need to invest in training and upskilling their cybersecurity teams to effectively manage cloud security.
- Cloud-Specific Threats: Cloud environments face unique threats, such as cloud misconfigurations, insider threats, and data exfiltration. Organizations need to implement specific security measures to mitigate these risks.
4. The Growing Threat of Ransomware
Ransomware attacks have become increasingly sophisticated and prevalent, targeting organizations of all sizes. Ransomware attackers encrypt sensitive data and demand payment in exchange for its decryption, causing significant financial and operational disruptions.
Ransomware Attack Trends:
- Targeted Attacks: Ransomware attackers are increasingly targeting specific organizations with valuable data and critical infrastructure, leveraging advanced reconnaissance and social engineering techniques.
- Double Extortion: Attackers are increasingly using double extortion tactics, stealing data before encryption and threatening to release it publicly if the ransom is not paid.
- Ransomware-as-a-Service (RaaS): The emergence of RaaS has made it easier for individuals with limited technical skills to launch ransomware attacks, further increasing the threat landscape.
Mitigating Ransomware Risks:
- Regular Backups: Maintaining regular backups of critical data is crucial to recover from ransomware attacks and minimize data loss.
- Employee Training: Educating employees about ransomware threats and best practices for identifying and avoiding phishing attacks is essential to prevent infection.
- Endpoint Security: Implementing robust endpoint security solutions, including antivirus software and endpoint detection and response (EDR) tools, can help prevent ransomware infections.
- Multi-Factor Authentication (MFA): Enabling MFA on all user accounts can significantly reduce the risk of unauthorized access and ransomware attacks.
5. The Importance of Cybersecurity Awareness Training
Cybersecurity awareness training plays a crucial role in protecting organizations from cyberattacks. By educating employees about common threats, security best practices, and the importance of reporting suspicious activity, organizations can foster a security-conscious culture and reduce the risk of human error.
Key Elements of Effective Cybersecurity Awareness Training:
- Engaging Content: Training programs should use engaging and interactive content, such as videos, simulations, and real-world examples, to effectively convey security concepts.
- Regular Refreshers: Employees should receive regular cybersecurity awareness training to reinforce key concepts and stay up-to-date on emerging threats.
- Scenario-Based Training: Scenario-based training allows employees to practice responding to real-world security incidents, building confidence and improving incident response skills.
- Phishing Simulations: Phishing simulations test employee awareness and help identify vulnerabilities in an organization’s security posture.
Benefits of Cybersecurity Awareness Training:
- Reduced Risk of Phishing Attacks: Training employees to identify and avoid phishing emails and websites significantly reduces the risk of social engineering attacks.
- Improved Security Practices: Awareness training encourages employees to adopt secure practices, such as using strong passwords, avoiding suspicious links, and reporting suspicious activity.
- Enhanced Incident Response: Educated employees are better equipped to identify and report security incidents, enabling organizations to respond quickly and effectively.
6. The Growing Need for Cybersecurity Talent
The cybersecurity industry is facing a severe shortage of skilled professionals, making it challenging for organizations to find and retain qualified cybersecurity talent. This talent shortage is driven by the rapid growth of the industry, the complexity of emerging threats, and the lack of qualified candidates.
Addressing the Cybersecurity Talent Shortage:
- Investing in Training and Education: Organizations need to invest in training programs to upskill existing employees and develop new cybersecurity talent.
- Attracting and Retaining Talent: Offering competitive salaries, benefits, and opportunities for professional growth is crucial to attract and retain top cybersecurity talent.
- Promoting Diversity and Inclusion: Creating a more diverse and inclusive cybersecurity workforce can help address the talent shortage and bring fresh perspectives to the industry.
Impact of the Talent Shortage:
- Increased Security Risks: The lack of skilled cybersecurity professionals can lead to vulnerabilities in an organization’s security posture, increasing the risk of cyberattacks.
- Higher Costs: Organizations may need to pay higher salaries to attract qualified cybersecurity talent, increasing cybersecurity costs.
- Slower Innovation: The talent shortage can hinder innovation in the cybersecurity industry, slowing down the development of new security solutions.
7. The Increasing Importance of Compliance and Regulations
Cybersecurity compliance and regulations are becoming increasingly stringent, requiring organizations to adhere to specific security standards and best practices to protect sensitive data and comply with legal requirements.
Key Cybersecurity Compliance and Regulations:
- General Data Protection Regulation (GDPR): The GDPR imposes strict requirements for the protection of personal data, requiring organizations to implement robust security measures and adhere to specific data processing principles.
- California Consumer Privacy Act (CCPA): The CCPA grants California residents specific rights regarding their personal data, requiring organizations to provide consumers with transparency and control over their data.
- Payment Card Industry Data Security Standard (PCI DSS): The PCI DSS sets security standards for organizations that process, store, or transmit credit card data, requiring them to implement specific security controls to protect cardholder data.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA regulates the use and disclosure of protected health information (PHI), requiring organizations in the healthcare industry to implement robust security measures to protect patient data.
Benefits of Compliance:
- Reduced Risk of Data Breaches: Adhering to compliance regulations can help reduce the risk of data breaches, protecting sensitive information and minimizing financial and reputational damage.
- Improved Security Posture: Compliance requirements often mandate the implementation of strong security controls, enhancing an organization’s overall security posture.
- Legal Protection: Compliance with relevant regulations can provide legal protection in the event of a data breach, mitigating potential legal liabilities.
8. The Growing Use of Blockchain Technology in Cybersecurity
Blockchain technology is gaining traction in the cybersecurity industry, offering potential solutions for secure data storage, identity management, and secure communication.
Applications of Blockchain in Cybersecurity:
- Secure Data Storage: Blockchain’s decentralized and immutable nature can provide a secure and tamper-proof platform for storing sensitive data, reducing the risk of data breaches.
- Identity Management: Blockchain can be used to create secure and verifiable digital identities, enhancing user authentication and reducing the risk of identity theft.
- Secure Communication: Blockchain can facilitate secure communication channels, ensuring data integrity and confidentiality.
- Cybersecurity Auditing: Blockchain can be used to record and audit cybersecurity events, providing a transparent and tamper-proof record of security incidents.
Challenges and Considerations:
- Scalability and Performance: Blockchain technology faces challenges in terms of scalability and performance, particularly when handling large volumes of transactions.
- Regulation and Compliance: The regulatory landscape for blockchain technology is still evolving, creating uncertainty for organizations seeking to adopt it.
- Technical Expertise: Implementing blockchain solutions requires specialized technical expertise, which can be a barrier for organizations without existing blockchain expertise.
Related Searches:
- Cybersecurity Trends 2023: This search explores the latest trends in cybersecurity, including emerging threats, evolving technologies, and industry best practices.
- Cybersecurity Industry Statistics: This search provides data and insights into the size, growth, and key players in the cybersecurity industry.
- Top Cybersecurity Companies: This search identifies the leading cybersecurity companies and their offerings, providing insights into the competitive landscape.
- Cybersecurity Jobs: This search explores the job market for cybersecurity professionals, including in-demand skills, career paths, and salary expectations.
- Cybersecurity Certifications: This search provides information about popular cybersecurity certifications, including their value, requirements, and benefits.
- Cybersecurity Best Practices: This search offers guidance on implementing effective cybersecurity practices, including security policies, risk management, and incident response procedures.
- Cybersecurity News: This search provides access to the latest news and updates on cybersecurity threats, industry trends, and emerging technologies.
- Cybersecurity Research: This search explores the latest research findings on cybersecurity threats, vulnerabilities, and mitigation strategies.
FAQs by Cybersecurity Industry Trends:
Q: What are the key benefits of adopting a zero-trust security model?
A: Zero trust security offers several benefits, including enhanced security posture, improved data protection, increased resilience, and reduced risk of unauthorized access. By eliminating the assumption of trust within a network, zero trust effectively reduces the attack surface and strengthens overall security.
Q: How can AI and ML be used to improve cybersecurity?
A: AI and ML algorithms can analyze vast amounts of data to identify suspicious patterns, predict potential threats, automate threat detection and prevention, and enhance incident response. These technologies can significantly improve the efficiency and effectiveness of cybersecurity measures.
Q: What are the main challenges associated with cloud-native security?
A: Cloud-native security presents challenges such as the shared responsibility model, the need for cloud security expertise, and the emergence of cloud-specific threats. Organizations need to address these challenges to ensure effective security in cloud environments.
Q: How can organizations protect themselves from ransomware attacks?
A: Organizations can mitigate ransomware risks by implementing robust security measures such as regular backups, employee training, endpoint security, multi-factor authentication, and network segmentation.
Q: Why is cybersecurity awareness training important?
A: Cybersecurity awareness training plays a crucial role in reducing the risk of human error by educating employees about common threats, security best practices, and the importance of reporting suspicious activity.
Q: What are the key challenges in addressing the cybersecurity talent shortage?
A: The cybersecurity talent shortage is a major challenge for organizations, driven by the rapid growth of the industry, the complexity of emerging threats, and the lack of qualified candidates. Addressing this shortage requires investments in training, education, and talent attraction strategies.
Q: What are the benefits of complying with cybersecurity regulations?
A: Compliance with cybersecurity regulations offers numerous benefits, including reduced risk of data breaches, improved security posture, legal protection, and enhanced customer trust.
Q: How can blockchain technology be used to enhance cybersecurity?
A: Blockchain technology offers potential solutions for secure data storage, identity management, secure communication, and cybersecurity auditing, leveraging its decentralized and immutable nature.
Tips by Cybersecurity Industry Trends:
- Embrace a proactive approach to cybersecurity: Instead of reacting to threats after they occur, organizations should proactively identify and mitigate risks by implementing comprehensive security measures.
- Invest in continuous learning and development: The cybersecurity landscape is constantly evolving, so it’s crucial to stay up-to-date on the latest threats, technologies, and best practices.
- Foster a security-conscious culture: Create a culture where security is everyone’s responsibility, encouraging employees to report suspicious activity and adopt secure practices.
- Collaborate with industry partners: Collaborating with other organizations, cybersecurity vendors, and government agencies can provide valuable insights and support in addressing cybersecurity challenges.
- Stay informed about emerging trends: Keep abreast of the latest cybersecurity industry trends and research findings to inform security strategies and stay ahead of the curve.
Conclusion by Cybersecurity Industry Trends:
The cybersecurity industry is facing a complex and evolving threat landscape, requiring organizations to adopt a proactive and comprehensive approach to security. Understanding the key cybersecurity industry trends is crucial for staying ahead of emerging threats and adapting security strategies to meet the evolving needs of the digital world. By embracing zero trust security, leveraging AI and ML, adopting cloud-native security, mitigating ransomware risks, investing in cybersecurity awareness training, addressing the talent shortage, complying with regulations, and exploring blockchain technology, organizations can build a more secure and resilient future.




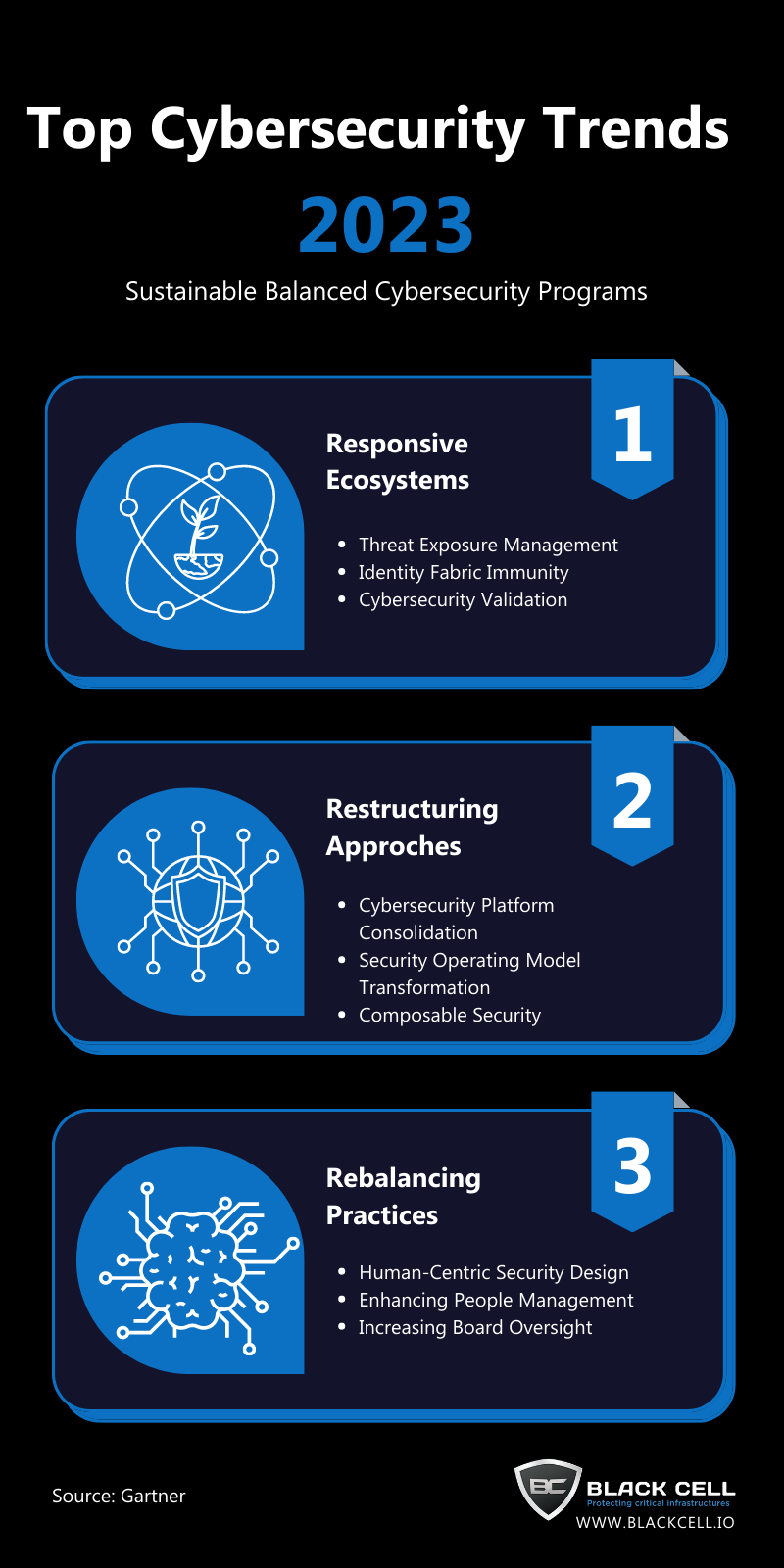
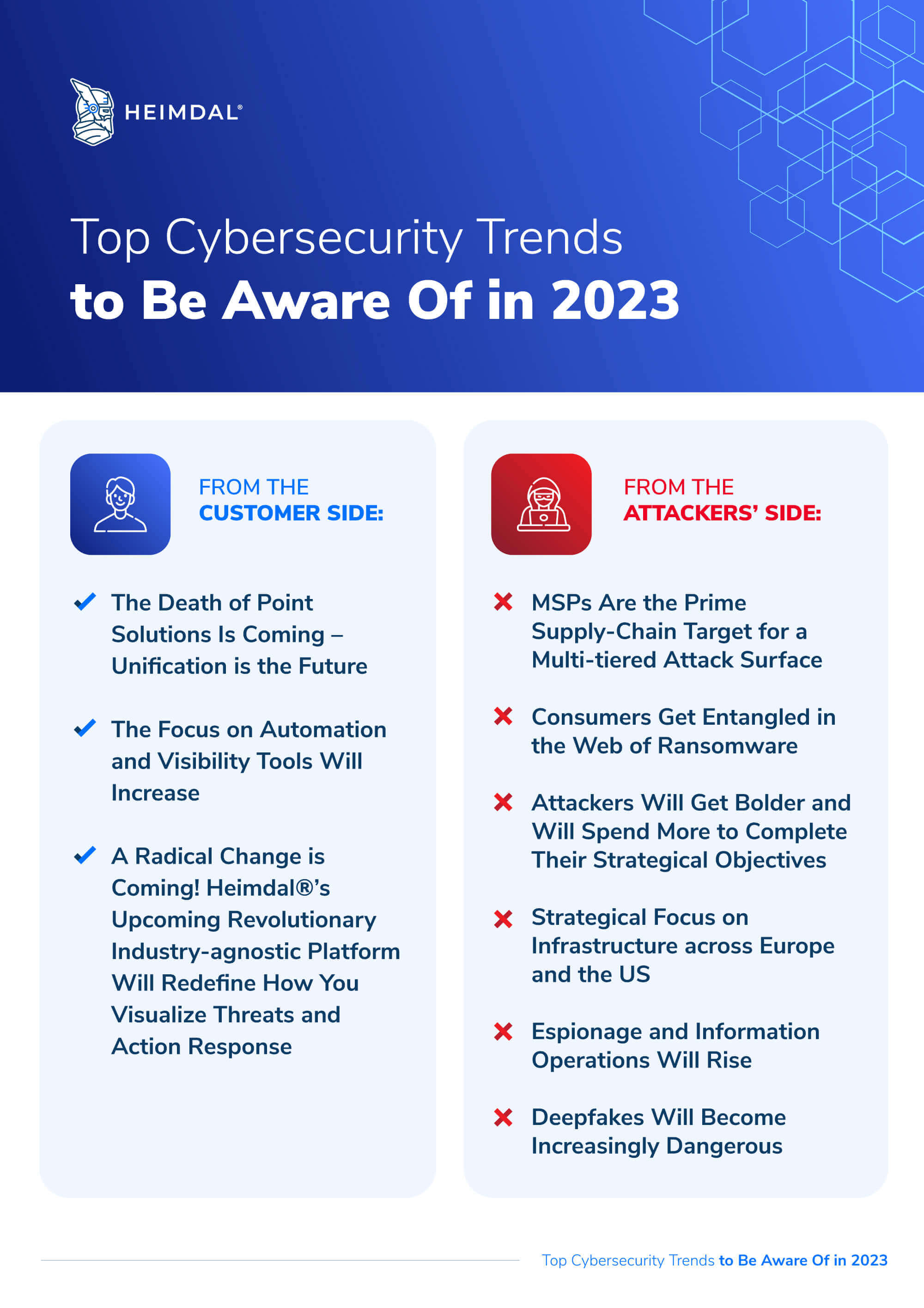
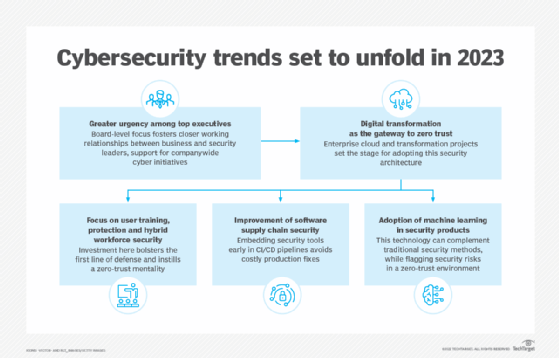

Closure
Thus, we hope this article has provided valuable insights into Navigating the Evolving Landscape: Cybersecurity Industry Trends in 2023. We appreciate your attention to our article. See you in our next article!